Why Does My Antivirus Say That Cryptomining Software Is Malware – Explore More!
Antivirus flags cryptomining software due to excessive resource use, cryptojacking risks, or malware association.
In this article, we’ll explore why antivirus programs often identify cryptomining software as malware, the risks associated with cryptomining, and how to navigate this issue safely and responsibly.
Table of Contents
Understanding Cryptomining Software:

Cryptomining software is a program designed to utilize your computer’s processing power to solve mathematical problems that validate cryptocurrency transactions. In return for their computational contributions, miners receive cryptocurrency rewards.
Mining software ranges from legitimate programs provided by trusted companies to potentially harmful versions distributed by cybercriminals.
Why Does Antivirus Flag Cryptomining Software:
Antivirus software relies on complex algorithms and databases to detect potentially harmful programs. Here are the primary reasons why cryptomining software is flagged:
Similar Behavior to Malware:
Cryptomining software often exhibits behaviors that are strikingly similar to malware. For example:
- High CPU/GPU Usage: Mining software uses significant computational resources, which is a common characteristic of malware like trojans and worms.
- Background Activity: Many miners operate in the background without explicit user permission, mimicking the stealthy behavior of malicious programs.
Association with Cryptojacking:
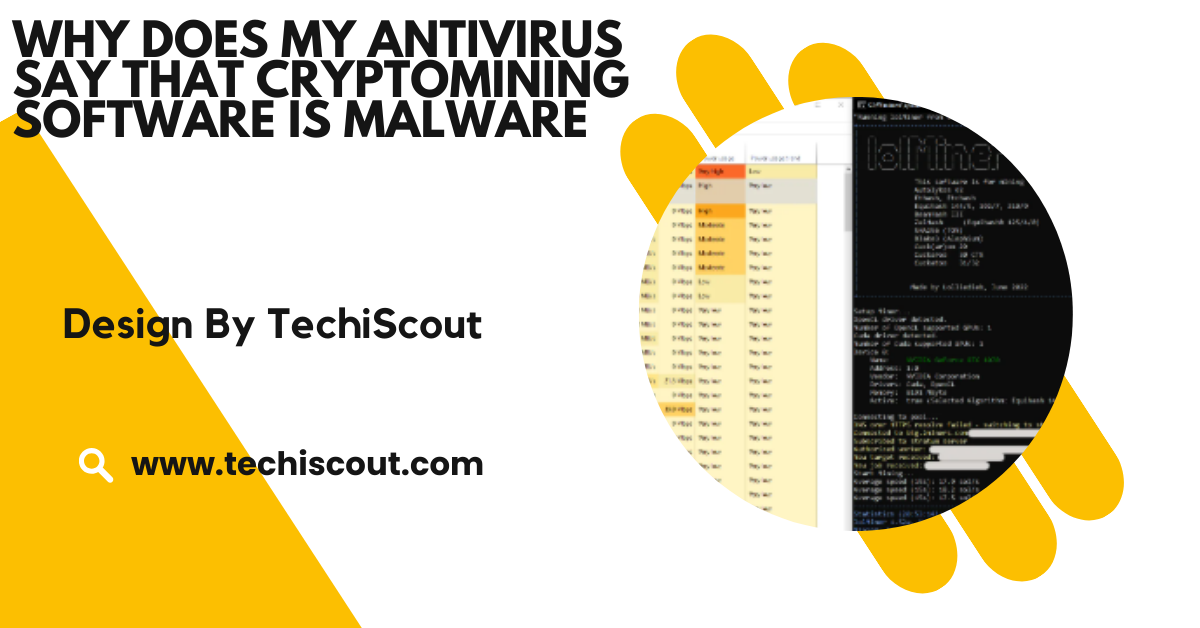
Cryptojacking is a cybercrime where attackers secretly install cryptomining software on a victim’s device without consent. The goal is to mine cryptocurrency for the attacker, often leaving the victim with slow devices and high electricity bills. Antivirus programs flag mining software to prevent potential cryptojacking threats.
Potential for Abuse:
Even legitimate mining software can be misused. Cybercriminals might repurpose well-known mining applications or distribute them in malicious packages. To err on the side of caution, antivirus programs often classify mining software as potentially unwanted programs (PUPs).
Code Similarities:
Some cryptomining software contains code that closely resembles malicious code snippets found in trojans, spyware, or ransomware. This similarity can trigger antivirus alerts, even if the software itself isn’t harmful.
User Protection Policies:
Antivirus software providers aim to protect users from high-risk behaviors. Since cryptomining can cause performance degradation, overheating, and excessive energy consumption, antivirus programs may flag it as a warning to users.
Is Cryptomining Software Always Malware:
No, not all cryptomining software is malware. However, distinguishing between legitimate and malicious software can be challenging. Here’s how to assess the legitimacy of cryptomining programs:
Source Verification:
- Only download mining software from official websites or trusted sources.
- Avoid third-party links or forums where modified versions might be shared.
Reputation and Reviews:
- Research the software’s reputation in the cryptocurrency community.
- Look for user reviews, testimonials, and independent assessments.
Digital Signatures:
- Check whether the software is digitally signed by a reputable company. This ensures its authenticity.
Permissions:
- Legitimate mining software will explicitly request your consent before installation and operation.
Read More: Is Cisco Fpr Software Or Hardware
Risks of Using Cryptomining Software
While cryptomining can be lucrative, it comes with several risks that justify antivirus warnings:
Resource Drain:
Mining software consumes a significant amount of processing power, which can lead to:
- Slower device performance.
- Overheating, potentially damaging hardware.
- Increased energy consumption and higher electricity bills.
Security Vulnerabilities:
- Malicious mining software may contain backdoors or exploit vulnerabilities in your system, leaving you exposed to further attacks.
Financial Loss:
- If you’re mining on a personal device, the operational costs may outweigh the rewards.
- Scams and fraudulent software can steal your mined cryptocurrency or compromise your wallet.
Legal Implications:
In some jurisdictions, cryptomining software could be restricted or regulated. Additionally, if your device is part of an unauthorized mining operation (e.g., cryptojacking), you may face legal consequences.
How to Safely Use Cryptomining Software:
If you intend to use cryptomining software, follow these best practices to minimize risks and avoid triggering antivirus alerts unnecessarily:
Use Trusted Antivirus Software:
- Keep your antivirus updated to recognize the latest threats.
- Configure the antivirus settings to whitelist your chosen mining software if you trust it.
Monitor System Performance:
- Regularly check your device’s temperature and resource usage to prevent overheating and performance issues.
Stay Updated:
- Use the latest versions of mining software to ensure security patches and optimizations are in place.
Avoid Public Networks:
- Always mine on secure, private networks to prevent interception or unauthorized access.
Educate Yourself:
- Stay informed about cryptomining trends, scams, and regulatory developments to make informed decisions.
What to Do If Your Antivirus Flags Cryptomining Software:
If you believe the flagged software is legitimate, here’s how you can proceed:
Double-Check the Source:
Verify that the software was downloaded from an official and reputable source. If unsure, it’s safer to avoid using it.
Whitelist the Software:
Most antivirus programs allow you to whitelist trusted applications. This will prevent future alerts while keeping your system protected.
Scan with Multiple Tools:
Use a combination of antivirus and antimalware tools to ensure the software is not harmful. Tools like Malwarebytes and VirusTotal can provide additional insights.
Consult the Community:
Reach out to cryptocurrency forums or communities to confirm the software’s legitimacy.
Contact Support:
If your antivirus repeatedly flags legitimate software, contact the antivirus provider’s support team for guidance.
Alternatives to Personal Cryptomining:
If managing cryptomining software feels overwhelming or risky, consider these alternatives:
Cloud Mining:
- Rent mining resources from a service provider instead of using your own hardware.
- Be cautious, as many cloud mining services are scams.
Staking:
- Participate in proof-of-stake (PoS) networks where you earn rewards by holding and validating cryptocurrency.
Cryptocurrency Trading:
- Invest in cryptocurrencies through exchanges without engaging in the mining process.
Mining Pools:
- Join a mining pool where multiple users share resources and rewards, reducing individual risk.
FAQ’s:
What is cryptojacking?
Cryptojacking is the unauthorized use of your device’s resources to mine cryptocurrency without your consent.
Why does my antivirus flag cryptomining software?
Antivirus programs flag cryptomining software due to its high resource consumption, potential for cryptojacking, or association with malware.
Can cryptomining software harm my device?
Yes, it can slow down your device, cause overheating, and decrease its lifespan due to excessive CPU or GPU usage.
How can I protect my device from cryptomining malware?
Use reliable antivirus software, avoid untrusted downloads, and monitor your device’s performance for unusual resource usage.
Is all cryptomining software dangerous?
Not all cryptomining software is dangerous; only unauthorized or malicious mining programs pose a significant risk.
Conclusion
Antivirus programs flag cryptomining software because of its potential misuse and association with malware. While legitimate cryptomining tools exist, their resource-intensive and sometimes opaque nature can raise alarms. Understanding the difference between legitimate and malicious cryptomining can help you make informed decisions about your device’s security.Protecting yourself against cryptojacking and cryptomining malware starts with vigilance, robust antivirus software, and adopting safe online practices.