Software Complexity Leads to Vulnerability – Explore Solutions!
Software complexity increases vulnerabilities; secure coding, simplified architecture, and regular audits mitigate risks effectively.
This article explores how software complexity leads to vulnerability, examines real-world impacts, and provides practical solutions to mitigate risks.
Table of Contents
Understanding Software Complexity:
Software complexity refers to the intricacy of a software system’s design, codebase, and architecture. This complexity stems from several factors:
Feature Overload:
Software development often aims to meet diverse user needs, resulting in numerous features. While these features improve functionality, they increase the risk of bugs and security loopholes.
Integration Challenges:
Modern software frequently integrates with third-party tools, APIs, and plugins. Each integration adds layers of complexity, making it harder to secure all components.
Codebase Entanglement:
As software evolves, developers might add new features without restructuring the codebase. This leads to tightly coupled components, increasing the chances of unintended errors.
Rapid Development Cycles:
The demand for frequent updates and new features can lead to rushed development and insufficient testing. Such practices often result in overlooked vulnerabilities.
Why Complexity Breeds Vulnerability:
Expanded Attack Surface:
Every new feature, integration, or line of code adds to the potential entry points for attackers. Complex systems are particularly vulnerable because each component must be secure to protect the whole.
Human Errors:
As complexity grows, so does the likelihood of human errors in development, testing, and deployment. Misconfigurations, unpatched bugs, and insecure code can create exploitable weaknesses.
Difficulty in Testing:
Testing becomes increasingly challenging as software complexity rises. Comprehensive testing is time-consuming and may fail to uncover hidden vulnerabilities, especially in interconnected systems.
Dependency Risks:
Software often relies on external libraries, frameworks, or third-party services. If any dependency is outdated or compromised, it jeopardizes the entire system.
Legacy Code Problems:
Legacy code often coexists with modern features in complex systems, creating a patchwork of old and new technologies. This mix can lead to compatibility and security issues.
Real-World Impacts of Vulnerabilities:
The vulnerabilities caused by software complexity have far-reaching consequences, including:
Data Breaches:
High-profile data breaches have exposed sensitive information belonging to millions of users. Complex software systems with inadequate security measures are prime targets for hackers.
Financial Losses:
Organizations face significant financial damage due to cyberattacks, including costs related to downtime, legal penalties, and loss of customer trust.
Reputational Damage:
A single vulnerability can tarnish an organization’s reputation, resulting in lost customers and diminished market credibility.
Regulatory Penalties:
Governments and regulatory bodies impose hefty fines on organizations that fail to secure their systems adequately, especially under laws like GDPR and CCPA.
Read More: iCUE Software
Examples of Complexity-Induced Vulnerabilities:
Equifax Data Breach (2017):
The Equifax breach exposed personal information of over 143 million people. The breach was attributed to a failure to patch a known vulnerability in a third-party software component.
Log4j Vulnerability (2021):
Log4j, a widely used logging library, contained a critical vulnerability exploited by attackers. Its widespread use across complex systems made mitigation a global challenge.
SolarWinds Supply Chain Attack (2020):
Hackers exploited vulnerabilities in SolarWinds software to infiltrate multiple organizations. The attack highlighted the risks associated with complex software supply chains.
Addressing Software Complexity to Reduce Vulnerabilities:
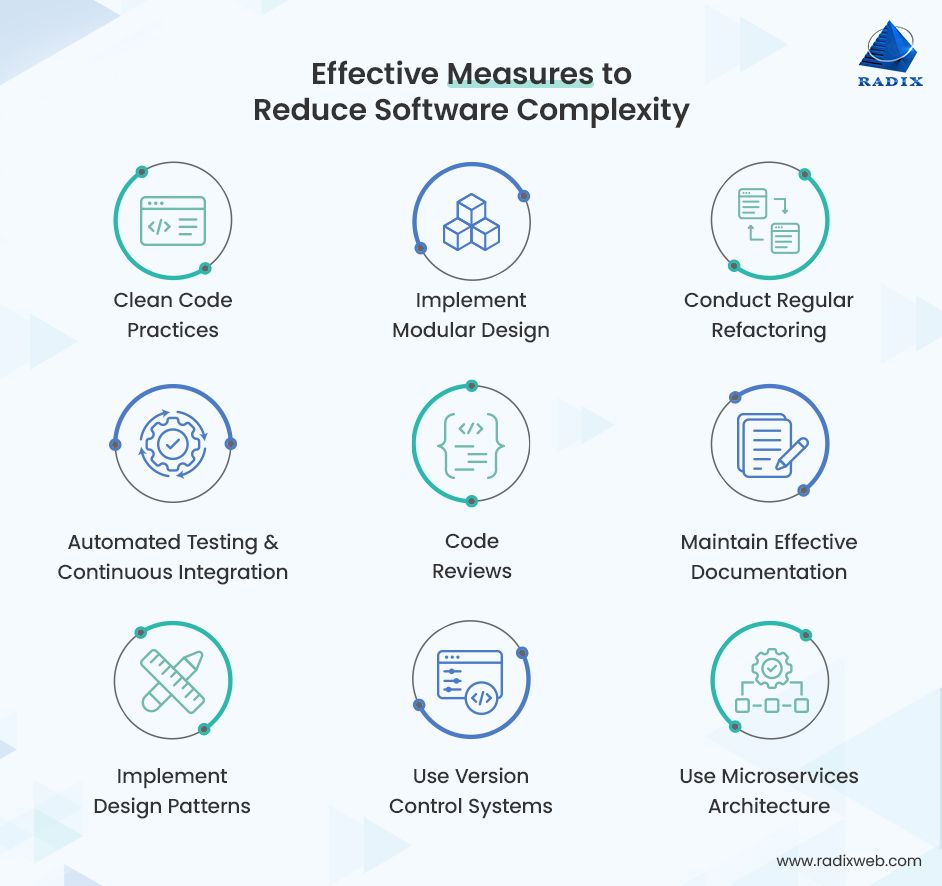
Secure Coding Practices:
- Adopt coding standards emphasizing security.
- Use code review tools to identify and fix vulnerabilities early in development.
Simplify Software Architecture:
- Avoid overcomplicated designs.
- Use modular and microservices architectures to isolate components and reduce interdependencies.
Regular Security Audits and Testing:
- Conduct penetration testing and vulnerability assessments frequently.
- Implement automated testing tools to identify issues in real time.
Dependency Management:
- Keep all software dependencies updated.
- Monitor third-party components for known vulnerabilities.
Continuous Integration and Continuous Deployment (CI/CD):
- Automate deployments to reduce manual errors.
- Incorporate security checks into CI/CD pipelines for proactive vulnerability detection.
Educate Developers and Teams:
- Train teams on secure coding practices and cybersecurity awareness.
- Promote a culture of security across the organization.
Emerging Technologies to Combat Vulnerabilities:
AI and Machine Learning:
AI and machine learning technologies offer advanced capabilities for identifying vulnerabilities in real time. These tools can automatically scan and analyze code, recognize unusual patterns or threats, and proactively predict potential attack vectors, offering superior protection against evolving cyber threats.
DevSecOps:
DevSecOps integrates security into every phase of the software development lifecycle. By incorporating security protocols early in the development process rather than as an afterthought organizations can address vulnerabilities before they evolve into significant issues.
This approach ensures continuous monitoring, automated security testing, and collaboration between development, security, and operations teams, strengthening the overall security posture of the software.
Blockchain Technology:
Blockchain provides an immutable ledger of transactions, which is particularly useful in securing software supply chains. By allowing data to be stored transparently and securely, blockchain can verify the integrity of code and prevent tampering.
This technology reduces risks associated with third-party dependencies, ensuring that software updates and integrations are traceable, secure, and resistant to fraud, making it a powerful tool in protecting against supply chain attacks.
Zero-Trust Architecture:
Zero-trust security is an emerging model that assumes no one, whether inside or outside the network, is inherently trustworthy. It requires continuous verification of every user and device attempting to access resources, minimizing the risk of breaches.
By reducing reliance on perimeter-based defenses and implementing strict access controls, zero-trust architecture ensures that only authorized users can access sensitive data and systems, even if a breach occurs.
Cloud Security Tools:
With the shift to cloud-based environments, cloud security tools are crucial in mitigating vulnerabilities. These tools offer advanced features like encryption, secure access management, and real-time threat detection to protect data and applications in the cloud.
Quantum Computing:
Though still in its early stages, quantum computing has the potential to revolutionize cybersecurity. Quantum algorithms can process vast amounts of data much faster than traditional computers, which can be used to crack encryption methods, but it also holds the promise of creating unbreakable encryption systems.
As quantum computing evolves, it will play a critical role in developing more secure systems to combat the vulnerabilities arising from traditional cryptographic methods.
FAQ’s:
1. Why does software complexity lead to vulnerabilities?
Complex systems have more components, increasing the chances of errors, unpatched bugs, and exploitable weaknesses.
2. What are the main risks of software vulnerabilities?
They can result in data breaches, operational downtime, financial losses, and reputational damage.
3. How can companies reduce software vulnerabilities?
By adopting secure coding practices, conducting regular audits, simplifying architecture, and managing dependencies.
4. What role do third-party integrations play in vulnerabilities?
Third-party tools increase the attack surface and can introduce risks if they are outdated or compromised.
5. How does automation help reduce vulnerabilities?
Automation streamlines testing, deployment, and monitoring, reducing human errors and improving security efficiency.
Conclusion:
Software complexity is an inevitable part of innovation. While it enables powerful functionalities and scalability, it also introduces vulnerabilities that can have dire consequences for businesses and users. By adopting robust security practices, simplifying architecture, and leveraging emerging technologies, organizations can mitigate risks and harness the benefits of complex software.Proactive measures and a culture of security are critical to safeguarding systems against the ever-evolving threat landscape.